What is a strong password?
Anyone with a digital life knows what a password is. It’s the secret key that completes an authenticator to gain access to online information. Whether it’s for your mailbox, your tax returns or to connect to your website’s management interface, you need a password.
As you already know, this password has to be strong.
We all used easy-to-remember passwords when we were starting out. Many people still do, and this article is for you! Examples: 123sun, Passw0rd!, NameSurname1980 (your year of birth), etc.
As you can imagine, these passwords are not secure.
Either because they are far too short and therefore quick to find in a brute force attack, or because they are already referenced in a database of passwords already in use, or can be guessed.
In a nutshell. To be strong, a password must
- be of sufficient length (I personally recommend at least 18 characters)
- does not contain words that are easy to guess, such as your name, your town, or anything similar
- has not already been used elsewhere
- contain a maximum of different character types (upper and lower case letters, numbers, special characters)
There are 2 types of password.
Classic passwords
They are made up of a sequence of random characters, such as R%9nJa^f*GyreSCXH2M6!tmJ
The advantage is that they are absolutely impossible to guess and contain different types of characters.
The disadvantage is that they are almost impossible for a human being to remember (or else you have a super memory).
There is a technique for generating such passwords and memorising them: using a matrix sentence (I just invented the term, don’t look it up).
For example, create and remember the following sentence: “My neighbour’s two cats are napping on the terrace every day and they’re so cute!”, and deduce the following password using upper case letters for each name: MN’s2CanotTed&t’rsc!
This gives you a pretty password with more than 20 characters, made up from a phrase that’s easy enough to remember.
This is just an example, of course, so don’t repeat it!
Passphrases
They are made up of several words strung together.
For example, you could use Hammer-Mole-Foot-Lasagnes-Fork as a passphrase that’s relatively easy to memorise with a bit of practice, and robust.
You can go a step further and add numbers after each word.
How to choose a password
Using a generator
To create a password, there are online generators (which do not store the results of generations, of course).
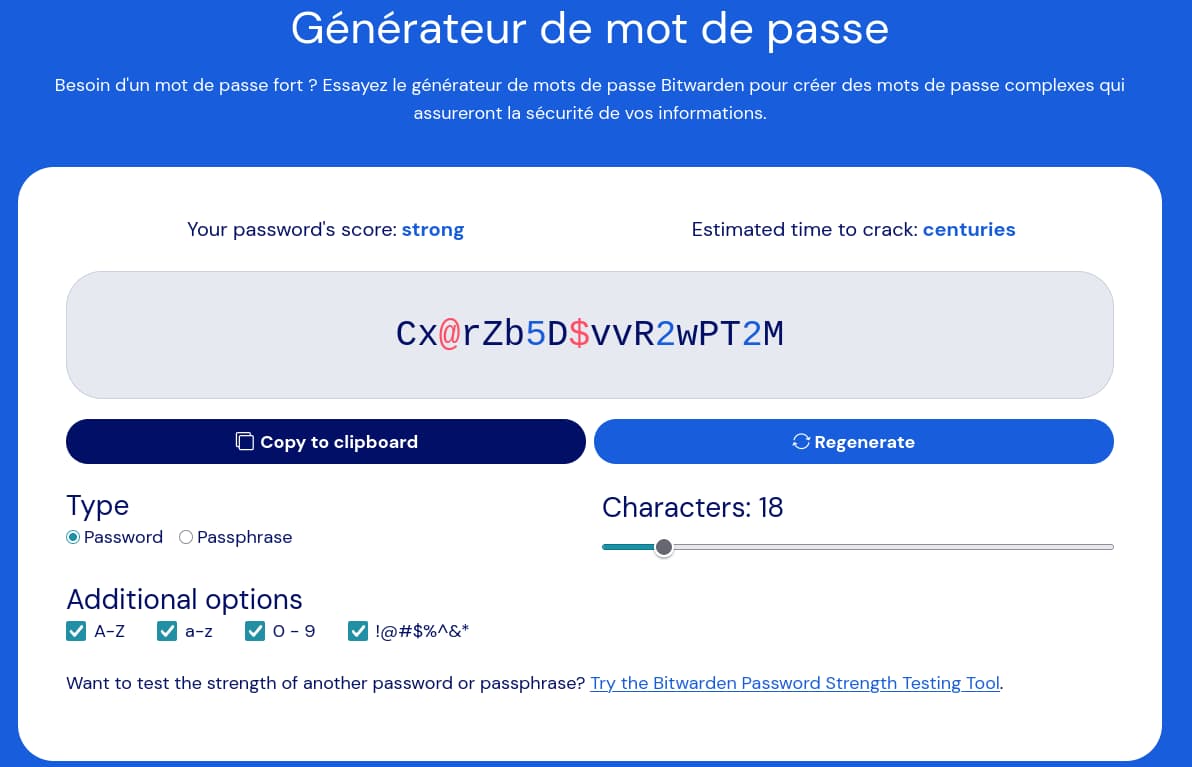
Remember to check the strength of your password. It would be a shame to generate a password that cracks in 5 minutes.
Check for data breaches
It is also very important to check that your password does not already exist in the data leaks listed.
In practical terms, this is probably the case if it is a weak password, or one that has already been used somewhere on a site whose data has been leaked.
You can enter your password on the HaveIBeenPwned site and you’ll find out. Note that good password managers do this job for you automatically.
I’ll talk about password managers a little further on.

How does a hacker find out your password?
I’m going to keep this part fairly short, the idea being to help you understand the important theoretical points and what happens when you create a password on a site.
Hashing
When you choose a password (when creating an account on an online site, for example), your password is never stored in clear text anywhere. This would be far too risky, as it would only be necessary to access the data on the server to find out your password.
Instead, your password is transformed into a “hash”. To do this, it passes through a complex hashing algorithm, which is unique in that it only works in one direction.
If you have a hash, you cannot trace it back to the password that created it.
And a given hash could only have been generated by a single password.
What happens is that it is the hash of your password that is stored on the server.
And if I try to log in with your account, the server hashes the password I’ve entered, and checks whether it matches the hash it has in memory. If it’s the same, that means it must be the right password that I’ve entered, and so the doors to your account open.
A case in point?
The 123sun password is transformed into $2a$12$JodVuPQubd9D5jCDPYpK.kKPEIAmp9hxRk.rq5AJJW42cUpJnFdW when hashed by Bcrypt.

You can have fun generating hashes online at bcrypt-generator.com.
Data leaks
In the event of a data leak, it is the password hashes that are recovered and circulated online.
On the other hand, your login details, telephone number, emails, etc. are generally stored in clear text, and can therefore be directly retrieved by hackers in the event of a data leak.
As a reminder, such leaks are extremely common, especially on very large platforms such as Facebook, or the sites of major companies such as Free.
As for Facebook, if it amuses you, you can check whether your phone number is circulating on the dark web because of the data they’ve leaked by visiting HaveIBeenZuckered.com.
The technique for finding a leaked password
So how will the hacker find your password?
As you can see, his task will be much easier if he has managed to find the hash of your password.
This is possible in the event of a security breach.
Now you know why it’s important not to choose a known password.
If the hash is part of the directory of previously leaked passwords, all you have to do is search this index to find your password immediately.
What if it’s not there?
How do I find a password that hasn’t been leaked?
The hacker will use software to generate hashes until he finds one that is identical to yours. They will then have found your password.
This is the brute force attack technique.
If your password is rather weak, it can be cracked quickly.
For example, let’s say your password is “123sun”. With a machine running smoothly, it will only take a few seconds to crack it. This is simply because the password is only 6 characters long, with no capital letters or special characters.
In reality, the software used to crack passwords is a little more sophisticated than that, and will use dictionary attacks, for example, and already knows the hashes of many existing words.
Softwares like John the ripper which is free and open-source let you audit the strength of a password by launching several types of attack.
Warning: password cracking software should only be used for educational purposes or for security audits.
Use a good password manager
If you have read the previous paragraphs, you should have understood the importance of having strong passwords for all your online accounts. And the importance of never re-using the same password. You should also have understood that it is humanly impossible to remember complex passwords.
That’s why you need a password manager to make sure you have good passwords.
Which one should you choose? There is no absolute answer, and several quality solutions exist. Here are just a few criteria that I think are important to consider:
- the software must be free and opensource and have been audited by independent experts (we’re talking about a tool that will store your precious passwords!).
- it must be able to be hosted wherever you want (for reasons of data control and digital sovereignty)
- it generates passwords on the fly (classic or passphrase)
- it allows safes to be shared with third parties
- offers dual-authentication procedures
- checks for data leaks, ensures that passwords are not re-used
- etc
Personally, I use and recommend Bitwarden with my eyes shut. It ticks all the boxes, is very intuitive, has desktop versions for Linux, Windows and Mac, and the smartphone application is also very well done. You can also simply import your passwords from your old password manager.
As a bonus, Bitwarden lets you share texts or files with a third party via a secure link.
The self-hosted version of Bitwarden is called Vaultwarden. In order to raise awareness and encourage Ikacode customers to keep their personal and professional data secure, they are offered free access for life following any web design or redesign service, with a Premium account to share vaults precisely within their various teams.
To find out more
This article has only scratched the surface of the subject of securing your online accounts.
There are many other techniques for hacking into an online account or recovering a password, and this article has simply presented one of them for the purposes of raising awareness and educating people about digital security.
There are still other measures you can take to limit the risks of your digital identity being hacked. Let’s look at just a few of them.
Implementing 2FA
The next step is double authentication, which can be done by sending an email, an SMS, a dedicated application that provides a code when the connection is attempted, or a passkey.
So even if your login and password fall into the wrong hands, it will be impossible for the attacker to connect to your account without this additional information.
As you can imagine, this is a measure that is implemented as standard for the client accounts of the websites I create for my clients.
Don’t share anything sensitive
Need to give someone your password?
Generally speaking, it’s better to create an account linked to this other person than to provide access to your own account. But in situations where this is not possible and you need to send a password, don’t do it via unsecured channels such as email.
Even if the person you’re talking to hasn’t been hacked, it could happen in the future. All the hacker would have to do is rummage through old emails to recover the password.
Use tools such as Bitwarden Send or KPaste for example.
Do not store anything in clear text
Finally, never store your passwords on your computer in “clear text”, i.e. without encryption. Forget the bad idea of saving your sensitive data in a spreadsheet or text document. Entrust this data to a password manager.
Oh, I forgot. The post-it note stuck to your screen is also a no-no!
Summary of best practice
In this article, we have seen that it is important to use only strong, non-leaked passwords, and not to re-use them. We have also seen that a good password manager makes your life easier and saves you time, as well as making your access more secure.
If you’re having trouble implementing these best practices, have any questions or would like some advice, don’t hesitate to ask for help in securing your digital life as quickly as possible. Prevention is better than cure!





